10 Tips for Creating a ML Based Cybersecurity System l.linklyhq.com/l/1tvrD #MachineLearning #ArtificialIntelligence #Cybersecurity #Algorithms #ThreatAnalysis #Data #SmartSystems


Hey TwitterFam! 🌟
Day 34: 'Diamond Model'
In this room, I delved into the core features of the Diamond Model of Intrusion Analysis, exploring the adversary, infrastructure, capability and victim aspects.
#TryHackMe #DiamondModel #IntrusionAnalysis #CyberSec
#ThreatAnalysis #CS


In today's digital landscape, understanding threat impacts is crucial for security.
Stay tuned for Zeron's insights on effective strategies.
#Zeron #Cybersecurity #CyberRisk #CyberRisk Posture #ThreatAnalysis #SecurityMatters


I purchased your amazing book yesterday Thomas Roccia 🤘 and it's so good. Raj Samani wrote such a great Foreward as well! Thank you for sharing your knowledge, sir! 👾 #threatAnalysis #TTP


🚨 #CyberAttacks are becoming increasingly sophisticated, making robust threat analysis a must. 🛡️ Explore the various methods and techniques in our latest post, seanfraser.io/blog/2024-04-2…
📝 #CyberSecurity #ThreatAnalysis


The Next Big Attack on America: How It Will Surpass 9/11
#NationalSecurity #Counterterrorism #USAThreats #TerroristAttacks #HomelandSecurity #USASafety #ThreatAnalysis #TerrorismPrevention #USASecurity #TerrorismInsights

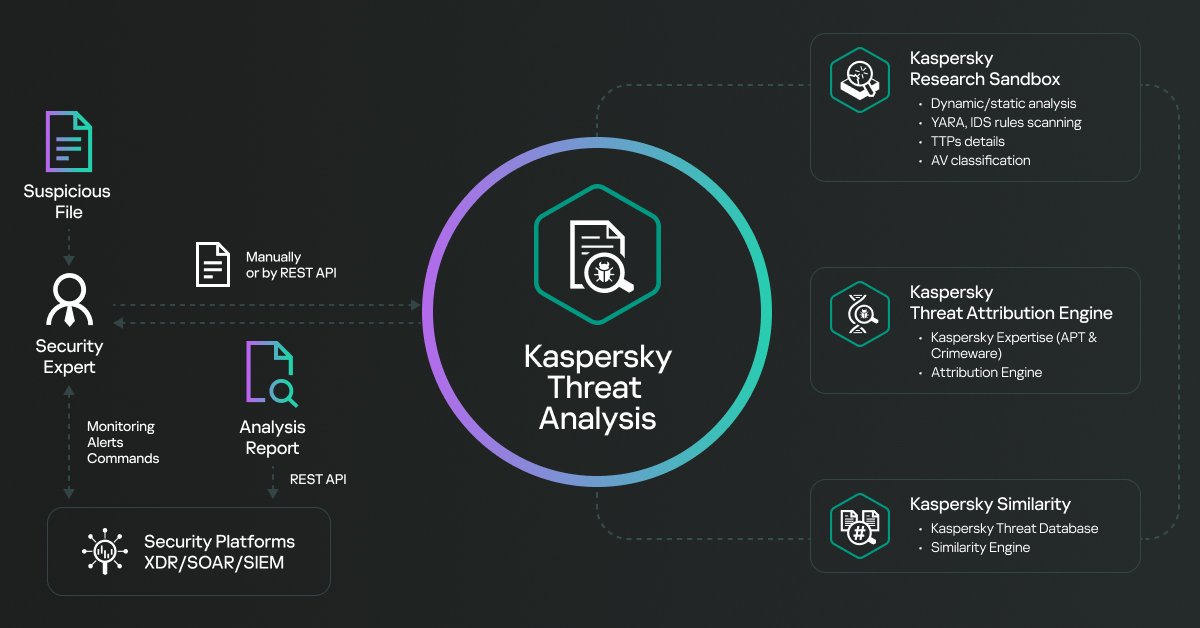
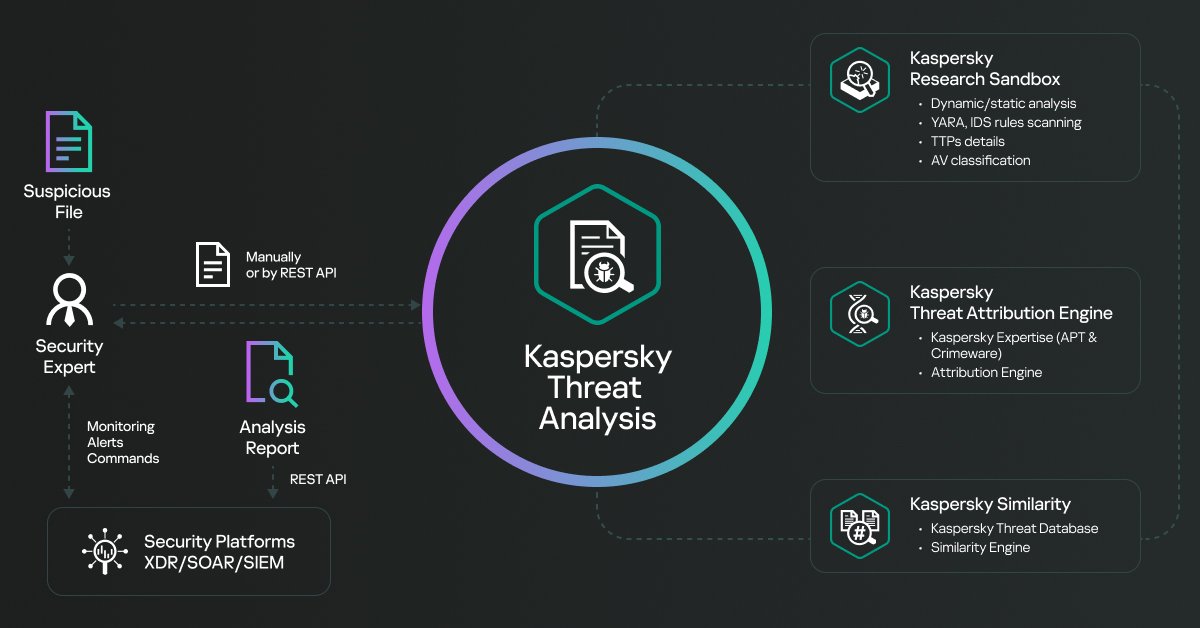
Explore Kaspersky Threat Analysis, integrating #threatintelligence , dynamic analysis, threat attribution, & similarity technologies. This hybrid approach ensures efficient #threatanalysis for informed decisions to secure your infrastructure. Learn more 👇 bit.ly/3HukLiu


Dive deep into the world of cyber threats and arm yourself with essential knowledge. From botnets and keylogging to zero-day exploits, explore the various tactics used by hackers to compromise networks and exploit vulnerabilities. #CyberSecurityInsights #ThreatAnalysis


whitehatsecurity.stream/News+Articles/…
#Cybersecurity #News #MalwareAnalysis #Threats #ThreatAnalysis


We are hiring Cybersecurity Threat Analysts for work in Denver, Colorado Springs, and Washington, DC. Go to invictusic.applicantpro.com/jobs/ to apply. To learn about Invictus go to invictusic.com. #cybersecurityjobs #threatanalysis #dcjobs #coloradojobs #remainunconquered


Explore Kaspersky Threat Analysis, integrating #threatintelligence , dynamic analysis, threat attribution, & similarity technologies. This hybrid approach ensures efficient #threatanalysis for informed decisions to secure your infrastructure. Learn more 👇 bit.ly/4b8Dde1

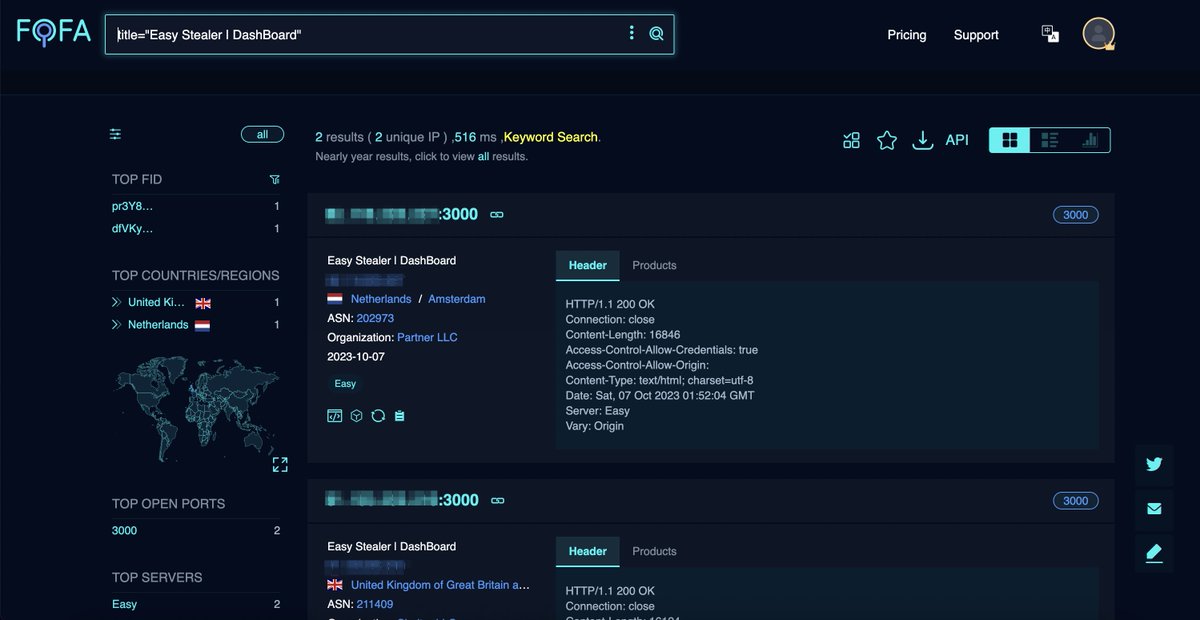
🔍 Bridewell CTI's latest report highlights 'Easy Stealer,' a new information-stealing malware currently in development. Great work!👍 Bridewell
FOFA was used for analysis.
👉Link: en.fofa.info/result?qbase64…
#Cybersecurity #EasyStealer #ThreatAnalysis #OSINT

Unveiling the Threat: Analyzing a Malware Downloader
#MalwareDownloader #Cybersecurity #RedTeaming #CobaltStrike #Dridex #ThreatAnalysis #RemoteControl #CyberThreats #MalwareDetection #DigitalSecurity


Splunk AI updates included specialized models for SecOps that detect and automatically respond to common issues
#SplunkAI #aiassistant #secops #devops #ITServiceIntelligence #Security #ThreatAnalysis #UserInterfaces #ThreatIntelligence #OpenAI #DevSecOps #Observability Splunk



Explore Kaspersky Threat Analysis, integrating #threatintelligence , dynamic analysis, threat attribution, & similarity technologies. This hybrid approach ensures efficient #threatanalysis for informed decisions to secure your infrastructure. Learn more 👇 bit.ly/4b5zxtI