🚨 Golang malware is on the rise 📈! Read Trellix blog post to discover how Ghidra scripts can streamline the analysis of this increasingly prevalent threat 💻🔒. Stay ahead of the curve! 👉 trellix.com/en-us/about/ne… #Cybersecurity #Golang #MalwareAnalysis #j2rsolves

1/5🧵 #AZORult or #Rultazo , #malware within the #Stealer family. Used by #FIN11 , #TA5050 ( #GracefullSpider ) and state-sponsored #GorgonGroup 🇵🇰
Full-Quick-Analysis: github.com/vc0RExor/Quick…
#threat #reverseengineering #RE #MalwareAnalysis

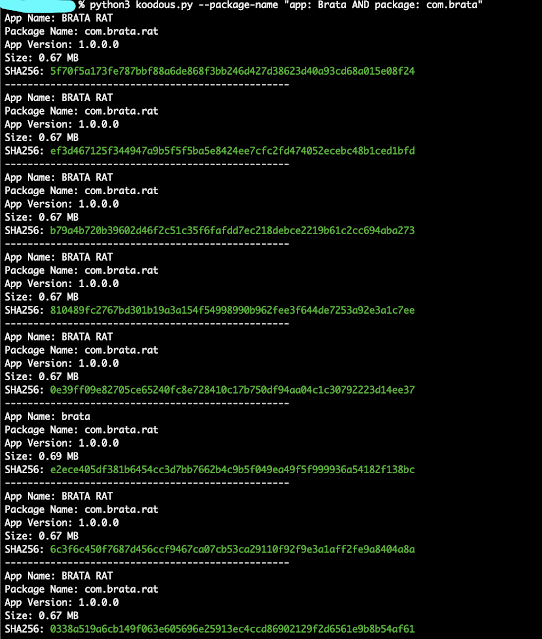
KoodousFinder - A Simple Tool To Allows Users To Search For And Analyze Android Apps For Potential Security Threats And Vulnerabilities #KoodousFinder #MalwareAnalysis #ReverseEngineering dlvr.it/SqqqS9

The #MalwareAnalysis session by Rushi is happening now! Don't miss the chance to #explore the different types of #malware , analysis #techniques , and real-world examples of how to analyze malicious software!
#MalwareAnalysis #SecurityResearch
#CyberAware
#nullahm


𝐀𝐰𝐞𝐬𝐨𝐦𝐞 𝐂𝐲𝐛𝐞𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 - 𝐂𝐨𝐥𝐥𝐞𝐜𝐭𝐢𝐨𝐧𝐬
RedTeam, PenTest, BlueTeam, SOC, MalwareAnalysis, Cloud Security and Others
#infosec urity #CyberSec #bug #BugBounty #infosec #bug bountytip #aws #cybersecuritytips #Hacking #redteam #Pentesting
🧵⬇️

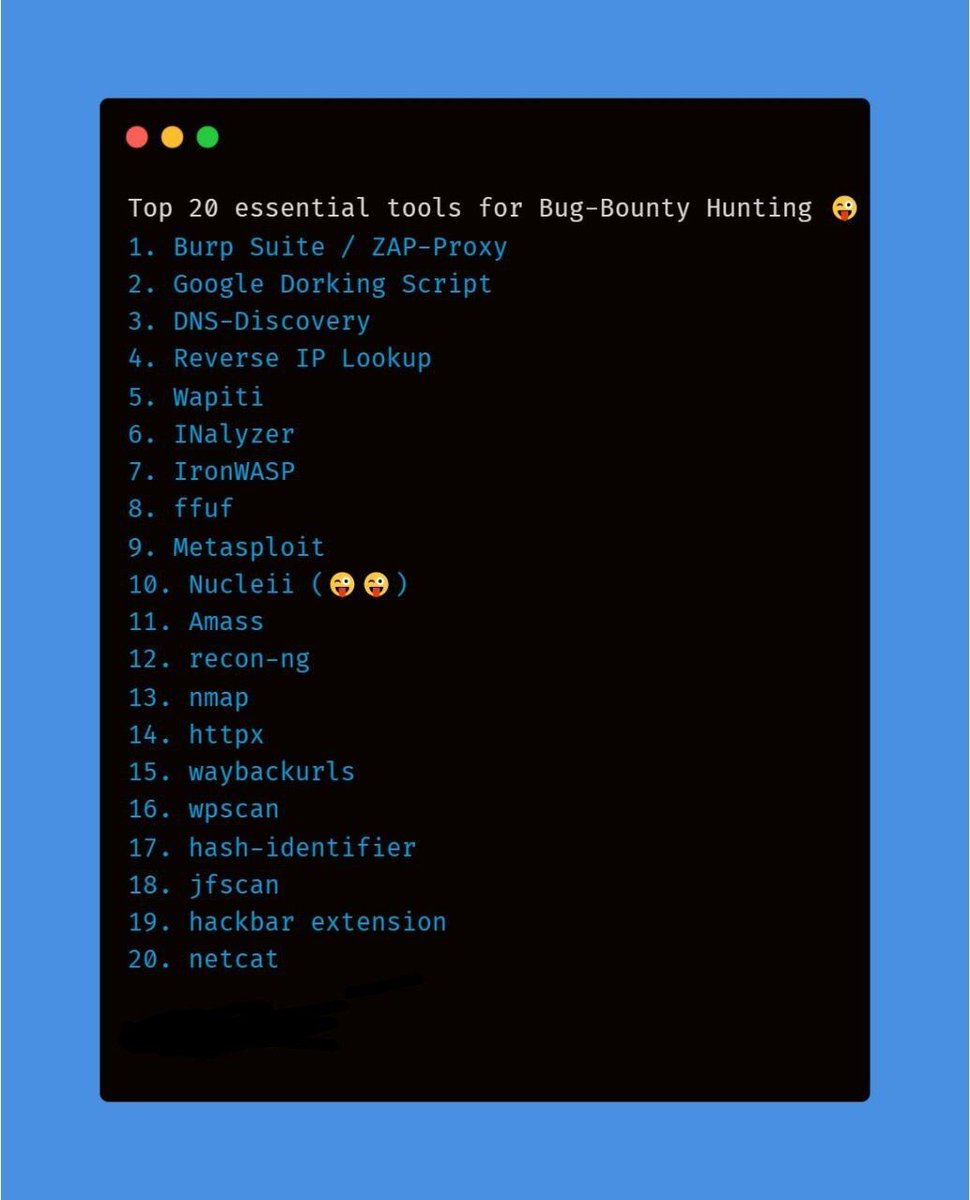
𝗧𝗼𝗽 𝟮𝟬 𝗘𝘀𝘀𝗲𝗻𝘁𝗶𝗮𝗹 𝗧𝗼𝗼𝗹𝘀 𝗙𝗼𝗿 𝗕𝘂𝗴 𝗕𝗼𝘂𝗻𝘁𝘆 𝗛𝘂𝗻𝘁𝗶𝗻𝗴
#hacking tools #malwareanalysis #metasploit #termux #bugbounty #hacking #cybersecurity
#cyberattack #cybersecurity awareness #ethicalhacking #hacker #infosec #kalilinux #pentesting

#Malware Analysis: #WhiteSnake #Stealer
cyberthint.io/malware-analys…
#threatintelligence #cyberintelligence #cti #malwareanalysis


Wish to unveil #malicious behavior of #attackers and find their #traces , join Moonbeom Park at #cyberDSA23 #sibersiaga23 .
Get your Early Bird ticket at sibersiaga.mil.my/attacker-behav…
#APT #malwareanalysis #infosec #cybersecurity #research

WordPress malware removal
Vulnerability Testing and Malware Analysis
About my services: fiverr.com/s/mBLbRb\
#removemalware #malware #wordpressmalware #malware analysis #malware removal

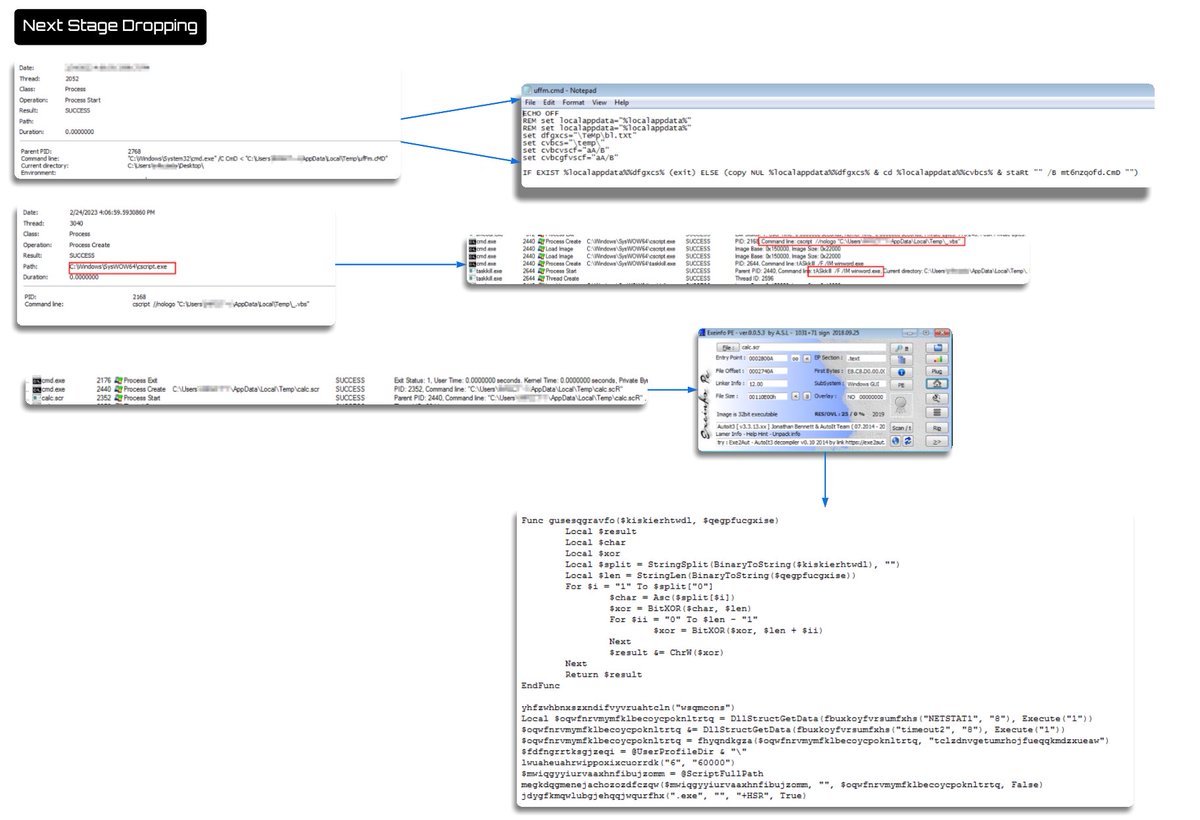
The #TrendMicro analysis of #Batcloak and #JLaive falls apart by comparing AV detection of a malicious binary to a malicious batch (ascii text) file. #malwareanalysis #journalism

github.com/cocomelonc/meow contains the results of all my research on cybersec practical cases from my blog #cybersec urity #cybersec #malware #malware analysis #blueteam #redteam #hacking #research #cybercrime #cryptography #programming

mssplab.github.io/threat-hunting… another source code analysis: Paradise ransomware #malware #malware analysis #malware attack #threatintelligence #threathunting #blueteam #redteam #purpleteam #research #hacking #cybersecurity #informationsecurity #cybercrime #ransomware

cocomelonc.github.io/malware/2023/0… next one in my blog. used by #glubteba malware in the wild #cybersec #informationsecurity #redteam #blueteam #malware #malware analysis #malware dev #malware attacks #cybercrime #hack ing #hack #purpleteam #programming #windows #cpp #research #win32api

Omar Amarin from Palo Alto Networks will give a #MalwareAnalysis workshop. This session will provide a comprehensive understanding of Malware Analysis, covering the fundamentals, as well as delving into Static and Dynamic Analysis techniques.
Join us🔒💻 cyberworkplace.tech/join-us-2/


We have released 'Defanger' - A #Notepad ++ plugin that defangs/refangs malicious IOCs
Check it out!
github.com/0x4427/Defanger
#malware analysis #reverseengineering #threathunting #infosec #cybersecurity #threatintel #malware #notepadplusplus #plugin #malware research #ioc

ChatGPT for SOC and Malware Analysis professionals: 3 Real-World:
any.run/cybersecurity-…
#malwareanalysis #reversing #ai #chatgpt #programming


The Hacker's Meetup Mumbai Presents Exploit Writing & Shell Coding!
#thehackersmeetup #thmmumbai #exploit #writing #shellcoding #threathunting #malwareanalysis #sysmon #webAppExploit #ReverseEngineering #Debugging #CyberSecurity #offensive #defensive



Learn how to perform DLL hijacking with custom-written DLLs in C++ and analyze the Indicators of Compromise (IOCs) left behind:
youtu.be/LDNexoA6jOo
#DLLHijacking #MalwareAnalysis #Cybersecurity