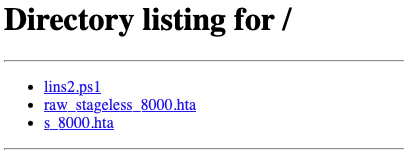
Ultimate List of Meterpreter Scripts
OccupytheWeb #metasploit #hacking #meterpreter
hackers-arise.net/2023/12/27/ult…





#metasploit #shell
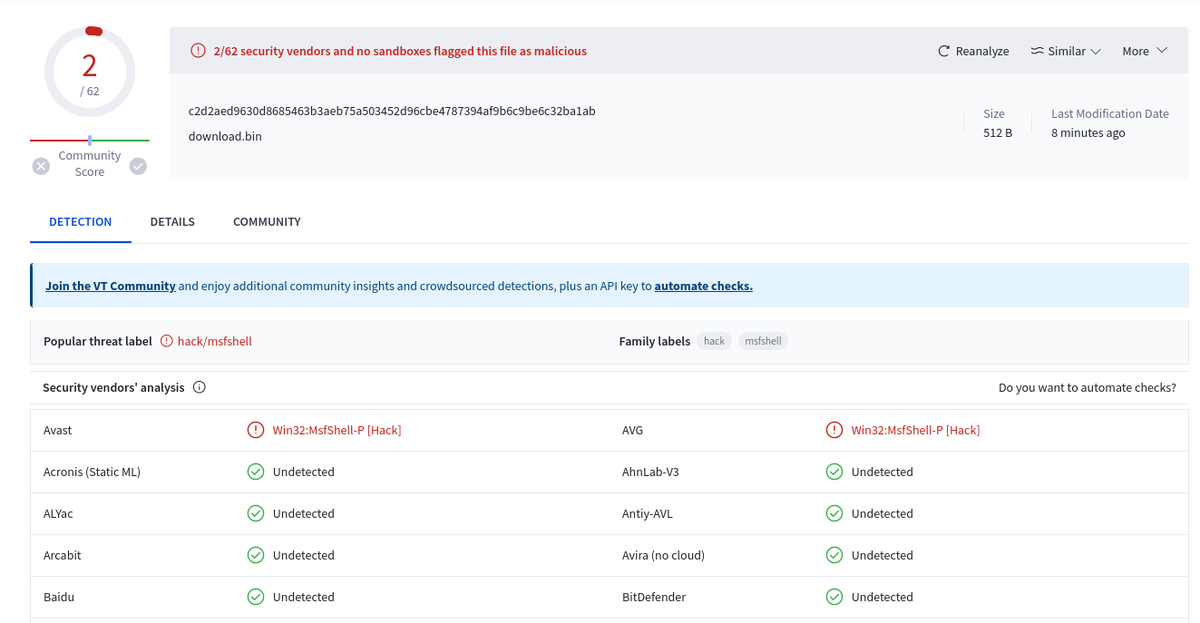
80.99.39.40:4587 - service banner - c2d2aed9630d8685463b3aeb75a503452d96cbe4787394af9b6c9be6c32ba1ab - msf-shell
AV Detections: 2/62 (by AVAST and AVG)
Malwarebytes Can you scan the file to check if it is really malicious?
It's odd having only 2 hits on VT.





عشان تختبر اختراق اي شبكة لاسلكية Wireless لازم تجهز لاب فيه هالادوات:
Wireshark
Scapy
Nmap
Aircrack-ng
Metasploit
#cybersexurity
#الامن_السيبراني

Bernies Soundlab ASCAP ©️®️™️🔬 1 (206) 586-9924 Metafix MetaverseVR Landscape Building Supplies Online RareOccurance Metasploit Project Meta Verse NFTs + Metaverse hunter metascript_solutions
Upgrade, Inc. Andrew Boswell えいむりぶ 🎹⭐️ Bernies Soundlab ASCAP ©️®️™️🔬 1 (206) 586-9924 Hands Like Houses
Houses of the Oireachtas - Tithe an Oireachtais
Bernies Soundlab ASCAP ©️®️™️🔬 1 (206) 586-9924 subdivisions SUBDIVISION DOORU (KPDCL) Throwing Fits


Metasploit, todo lo que debes saber sobre esta herramienta.
#ciberseguridad #hacking #hacker #metasploit
achirou.com/metasploit-la-…

TOP Cybersecurity Tools #cybersecurity #CybersecurityTools #Nmap #Wireshark #Metasploit #fyp #foreducationalpurposesonly